What is the Cyber Security?
Well, there is no boring two-line definition of cybersecurity here you get a proper explanation.
Let me first define the term “Cyber”:
In simple terms, Things that are related or connected to the Internet, Infomation, Technology, Data, Network, application, or computer are referred to as “Cyber”.
Ok, the actual question, what is cybersecurity?

Computer security is the protection of computer systems and networks from information disclosure, theft, or damage to their hardware, software, or digital data, as well as from the interruption or misdirection of the services they provide.
So in simple terms,
Cyber security is a process or method to protect your data such as login credentials, email, phone number, from unwanted access.
Pro tip: Cyber security is also known as Information technology security (not Information security).
Latest stats about Cyber Security?
I already published a whole article about stats of cybersecurity but here I want to share some important stats:
- 95% of cyber security breaches happen due to human mistakes.


- The average salary of a Certified Ethical Hacker is $83,591 per annum.
- The total cost of committed cyber-crimes globally will reach $10.5 trillion by 2025.
- 92% of malware is distributed through email.
- 77% of businesses do not have a Cyber Security Incident Response plan.
- 3.5 million unfilled cybersecurity jobs by 2021.
We have some amazing facts about stats of cybersecurity if you are interested go and check it out, cyber security stats.
Why Cyber Security is important?
Cybersecurity is important because it protects all data from theft and unwanted access. This includes sensitive data, personally identifiable data, personal data, financial data, or intellectual data.
Here I will break down some of the major benefits of digital marketing.
- Fast changes in technology.
We know technology is evolving day by day, AI and ML become more powerful. We are trying to automate our work, blackhat hackers also.
Just imagine a day when there is an ML algorithm that automatic able to learn new attacks and trick us. That’s scary, right?
- Damage to business.
All (Almost) well know companies had already faced at least one successful cyber attack. To ensure the company does not face any cyberattacks, implement a proper cybersecurity plan.
- Many Cyber security trades are faced by individuals.
No description is needed I think.
- The total cost of committed cyber-crimes globally will reach $10.5 trillion by 2025.
As I already mentioned in the stats above. The total cost of committed cyber-crime globally will reach $10.5 trillion by 2025 (predicted), that why we must have to secure our user’s data by following cyber security principles.
Ok look, there are more things why cybersecurity is important but I think is this is enough for this, Let me jump into 2 main questions, how you can start your career in cybersecurity and how to implement cyber security for your business.
How to get into cyber security? (Career)
To get into Cyber security, you just have to follow this step-by-step small guide:
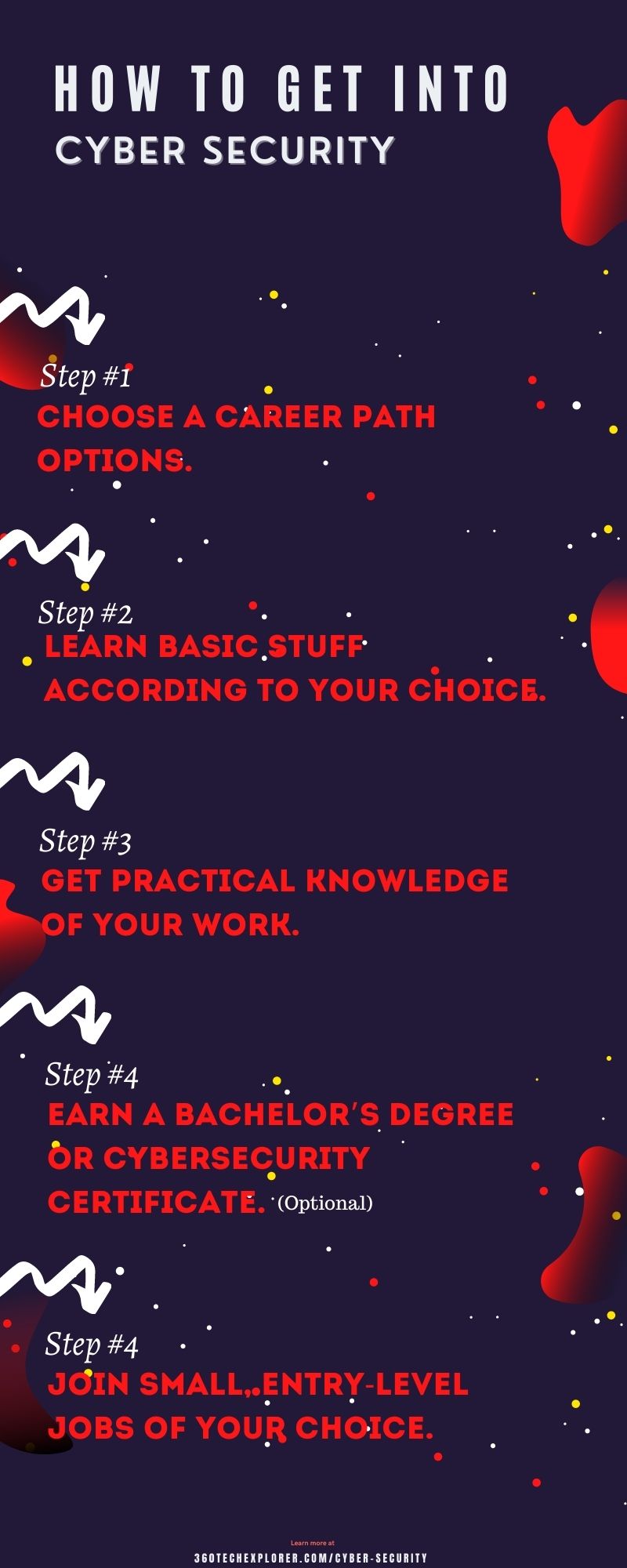

Step #1
Choose a Career Path Options.

Look, Cybersecurity is a very broad industry, there is a lot of work or jobs, So you have to narrow down exactly which career path or job you like to do.
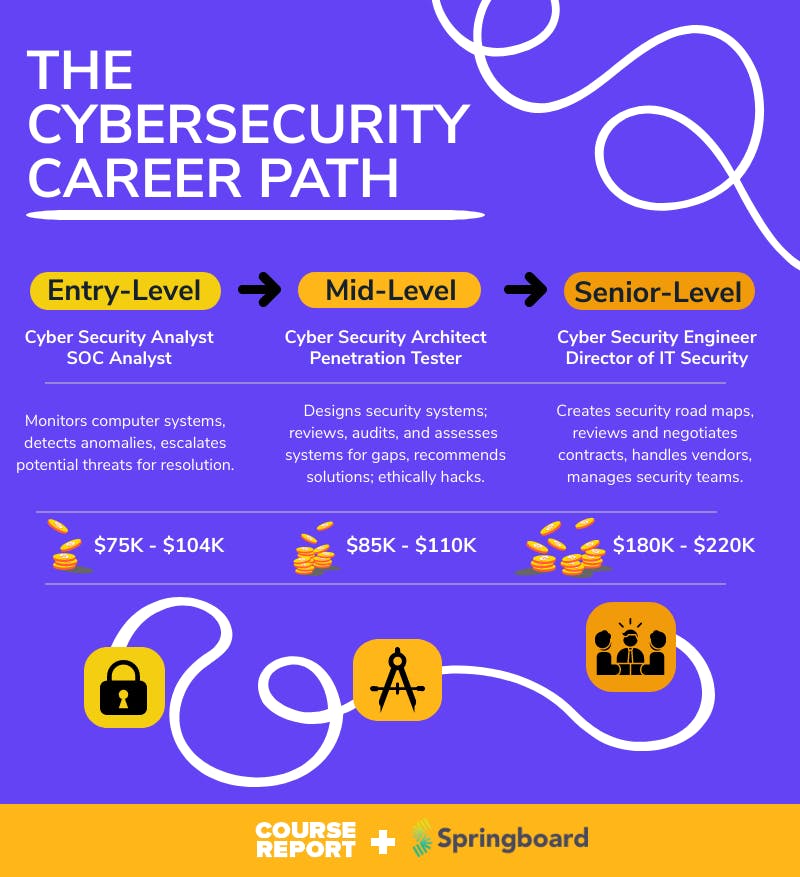
Major Cybersecurity jobs roles:
- Cyber security analyst.
Cyber security analysts (also called information security analysts) create a cybersecurity plan to protect a company’s computer networks and systems, They keep constant tabs on threats and monitor their organization’s networks for any breaches in security.
- Penetration Tester (Ethical Hacker)
A penetration tester (also called Ethical Hacker) is someone who tries to break into or find possible exploits in a company’s computer networks and systems. You can think of them as a type of hacker.
- Network administrator
A network administrator is a person designated in an organization whose responsibility includes maintaining computer networking and connectivity.
Other major IT Jobs:
- Computer Programmer
- Computer Software Engineer
- Computer Support Specialist
- Computer Systems Analyst
- Database Administrator
- IT Technician
- IT Technical Support
- IT Customer Service
- Network Administrator
- Network Engineer
- Network Systems & Data Analyst
- System Administrator
- Web Administrator
Research about them and choose the right field for you.
After choosing the right career path or job for you now you have to deep dive into it like WHAT SKILLS ARE NEEDED or WHAT WILL BE YOUR RESPONSIBILITIES. All that kind of stuff
Step #2
Learn basic stuff according to your choice.
This point where actual hard work is needed.
As you did basic research about your job now you have to learn all that basic stuff (by yourself or online courses).
Youtube doesn’t allow tech hacking that why you never get advanced stuff on youtube, yes they allow basic but I recommend you to use other FREE resources mention below.
Some of the FREE learning resources:
- Foundations of Cybersecurity course by Springboard.
- Cybrary
- Hackersploit YouTube Channel (I don’t recommend youtube for cybersecurity)
There are some other great resources as well do.
Our website is also a place where you get updates or tutorials about cybersecurity, click here to get all cybersecurity updates in your email.
Step #3 (Very Important)
Get practical knowledge of your work.
I highly recommend you gain as much practical experience as you can. Even if you’re not in IT, you can accomplish a lot with self-directed learning and guided training.
Step #4 (Optional)
Earn a bachelor’s degree or Cybersecurity certificate.


Having a degree or certificate just adds one plus point to your resume.
Get a Bachelor’s degree in Computer science or IT-related field. (THIS IS OPTIONAL)
The next thing you need to do is earn some basic cybersecurity certificates (go with CEH certificate) (THIS IS OPTIONAL BUT I HIGHLY RECOMMEND TO DO IT)
Note: Don’t try to crack CCIE, CCNA, or any other advanced cyber certification at this point. (If you are not sure go with CEH)
Step #5
Building Your Cybersecurity Resume.
I assuming you already completed some online courses or get knowledge about your field in cybersecurity.
Now you just have to build your amazing resume. Let’s build your resume together.


Here is a checklist for your cybersecurity resume.
- Name
- Email or phone number
- IT Skills
- IT Certifications
- IT Achievements
- College or Degree (If have)
- Old IT job experience (If have)
Pro tip: Make your resume clear and decent in design.
Step #6
Join small, entry-level jobs of your choice.

Now you have to get jobs. Just search for some entry-level good company and work with them don’t waste your time by waiting for your dream company job.
How to get a job in cyber security?
Ask your friend and family, Or Create a profile on an online work website such as UPWORK or LINKEDIN. Participate in interviews as much as you can.
Hey look, a lot of think that their knowledge is enough but it isn’t so if you didn’t get a job, follow step #2 and step #3 again.
Step #7
Learn more advanced stuff according to your choice.


You got a job it doesn’t mean you’re done, you still have to learn.
Live as if you were to die tomorrow. Learn as if you were to live forever.
by Mahatma Gandhi
At this point, you have to learn advanced stuff.
Do your own research or you can just simply ask about their experience and learning.
Step #8 (Important)
Get more practical knowledge of your work.
Implement what you are learning from the above step, get practical knowledge about advanced stuff and topics in your field.
Step #9(Optional)
Earn a master’s degree or some more reputed cybersecurity certificates.
Having a master’s degree or reputed certificate just adds plus points to your resume.
Get a master’s degree in Computer science or IT-related field. (THIS IS OPTIONAL)
The next thing you need to do is earn some advanced reputed cybersecurity certificates such as CCIE, CCNA.
NOTE: Don’t get into CCIE or CCNA directly, first research your field then decide.
Step #10
Update Your Cybersecurity Resume and apply for your dream job!
You’re done (Not really!).
Now if you want to change your company do it.
How to implement cyber security for your business or Project?


Cyber security includes a lot of stuff such as the Right network configuration, IAM, Data protection, bugs, and a lot of things.
As a business owner, I recommend you hire an agency or hire Cybersecurity guys.
I know It’s not FREE but it’s not more costly than your losing customer data and trust.
Here are few important things to do with your business.
- Train employees in security principles
- Keep your network private as much as you can.
- Review Latest Cybersecurity Cases
- Create a mobile device action plan
- Hire an agency or cybersecurity expert so they can guide you in the right direction.
Tip for hiring a cybersecurity expert or agency.


- Look for the Right Amount of Experience & Training
- Focus on Continuous Learning & Upskilling
- Be willing to train candidates after they’re hired
- Secure software development skills
- Ability to detect unauthorized intrusion on systems via network traffic, unusual activity, or physical threats
- etc.
Cyber security tips.
You will get rid of 90%-95% of all cyberattacks by just following these tips:
- Keep software up-to-date
This is the most common and easy one but still lot of people do not follow this. Most of the time company release their updates due to security issues or bugs. So make sure you use only the latest version of the application.
NOTE: Latest is not BETA
- Use complex password
You know my password length is 15 characters long that includes: special character, number, and alphabet. I highly recommend you choose a strong password.
- Avoid Phishing scams
Few identifiers of phishing pages:
- Without HTTPS.
- Give something for free that is paid.
- Untreated or unknown brand
- Ask for a social account password (instead of a direct social login button)
- Backup your data
This saves you tons of money because sometimes our important data hacked, delete, or get into a ransomware attack. In that situation, our backup is very useful for us.
There is a lot of other things to do as well 🙂
Types of cyber security?
Did you know there are different types of cyber security? Let me break them down so you can protect your organization and your personal information as well.
Internet of things (IoT) security


IoT refers to a wide variety of critical and non-critical cyber-physical systems, like appliances, sensors, televisions, wifi routers, printers, and security cameras.
Internet of Things security focuses on protecting your internet-enabled devices that connect to the internet. IoT security is the safety component tied to the Internet of Things, and it strives to protect IoT devices and networks against cybercrime.
Application Security
Application security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked. Application security may include hardware, software, and procedures that identify or minimize security vulnerabilities.
Cloud Security


Cloud security is the protection of data stored on cloud computing platforms from theft, leakage, and deletion. Methods of providing cloud security include firewalls, penetration testing, obfuscation, tokenization, virtual private networks (VPN), and avoiding public internet connections.
Network Security


Network Security is the process of taking physical and software preventative measures to protect the networking infrastructure from unauthorized access or improper disclosure, thereby creating a secure platform for computers, users, and programs to perform their permitted critical functions within a secure environment.
Types of cyber-attacks?
Malware

Malware is the collective name for several malicious software variants, including viruses, ransomware, and spyware. Shorthand for malicious software, malware typically consists of code developed by cyberattackers or hackers, designed to cause extensive damage to data or to gain unauthorized access to a network.
Types of Malware:
Virus
Worms
Spyware
Trojans
Ransomware
Phishing


Phishing is a cybercrime in which a target or targets are contacted by email, telephone, or text message by hackers posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking, and credit card details and passwords.
Denial-of-Service (DOS) Attack
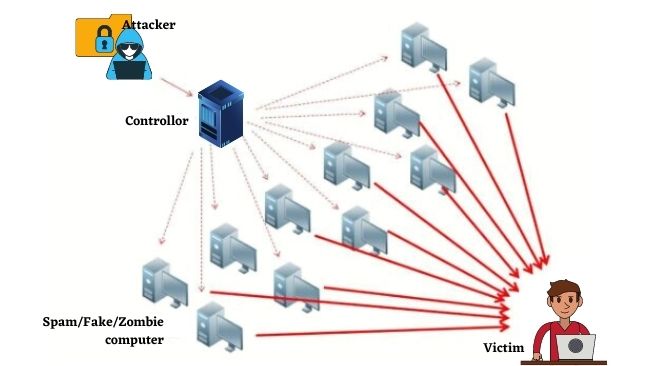

A Denial-of-Service (DoS) attack is an attack meant to shut down a machine, network, or website, making it inaccessible to its intended users. DoS attacks accomplish this by flooding the target with traffic or sending it information that triggers a crash.
SQL Injections
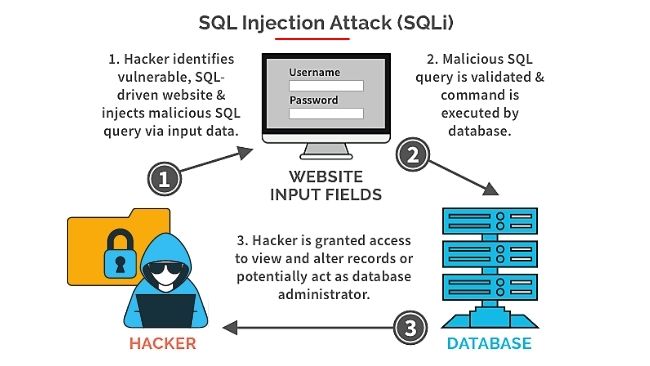

SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its SQL database. It generally allows an attacker to view data that they are not normally able to access directly.
Cross-site Scripting
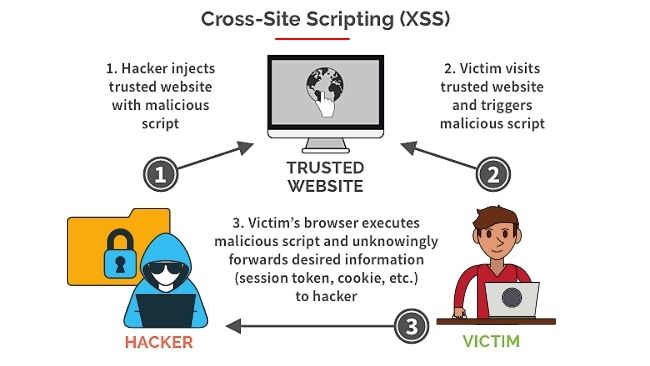

Cross-site Scripting (XSS) is a client-side code injection attack. The attacker aims to execute malicious scripts in a web browser of the victim by including malicious code in a legitimate web page or web application.
What are the challenges in cyber security?
Well, there are a lot of challenges in cyber security but here we discuss only major ones.
- AI and ML attack
AI and ML have become more powerful. We are trying to automate our work, blackhat hackers also. Even some tasks of black hat hacking are have been already automated. Our task to prevent this. And I think we need something like an automated algorithm that automatically able to learn cybersecurity and protect us. (Don’t get me wrong)
After that you may have a question: Will cybersecurity jobs get automated or at risk.
- Phishing attack
Phishing attack is the most common attacks. The is a challenge to develop something that bypasses phishing attacks.
- Crypto attacks
Crypto is getting more common these days but with this, black hat hackers also doing crypto attacks.
Even most of the payments of ransomware attacks are done by Bitcoin (crypto).
- Ransomware attacks
Ransomware affects a lot of businesses (as well as individuals) a few of the last few years (2018-2020), ransomware is also a big challenge for cyber security.
General FAQ about Cyber Security.
What is cyber security?
Computer security is the protection of networks from information disclosure, theft, or damage to their hardware, software, or digital data. In simple terms, Cyber security is a process or method to protect your data such as login credentials, email, phone number, from unwanted access.
How much do cyber security make?
How much does cyber security earn? Cybersecurity analysts pulled in an average annual of $83,591. PayScale, on the other hand, reports that those in the field make an average salary of $75,746 per year, with salaries ranging from as low as $51,000 to as high as $117,000.
Is cyber security hard?
That depends on the person who is trying to learn cyber security. For some, it will be relatively easy, for others frustratingly hard.
First of all, what is your background? If you already work with computers either as a programmer, or perhaps even a web developer, then you’ll have a good starting point to learn cyber-security. Although even this is by no means a guarantee that you’ll learn it.
How to get a job in cyber security?
Earn a bachelor’s degree in cybersecurity, information technology, computer science, or a related field, Complete an internship to obtain experience in a computer-related field then Gain special credentials by obtaining certification after that Pursue an entry-level position, in general, IT or security.
What does a cyber security analyst do?
Cyber security analysts plan and carry out security measures to protect a company’s computer networks and systems, according to the BLS. They keep constant tabs on threats and monitor their organization’s networks for any breaches in security.
Is cyber security a good career?
Again,
It depends on your background, If you already work with computers either as a programmer, or perhaps even a web developer, then you’ll have a good starting point to a cyber-security career. Although even this is by no means a guarantee that you’ll start it.
General Cyber Security Terms.
Penetration testing
Penetration testing also called pen testing or ethical hacking is the practice of testing a computer system, network, or web application to find security vulnerabilities that an attacker could exploit. Penetration testing can be automated with software applications or performed manually.
Clickjacking
Clickjacking is a malicious technique of tricking a user into clicking on something different from what the user perceives, thus potentially revealing confidential information or allowing others to take control of their computer while clicking on seemingly innocuous objects, including web pages.
Rootkit
A rootkit is a collection of computer software, typically malicious, designed to enable access to a computer or an area of its software that is not otherwise allowed and often masks its existence or the existence of other software. The term rootkit is a compound of “root” and the word “kit”.
Firewall
A Firewall is a network security device that monitors and filters incoming and outgoing network traffic based on an organization’s previously established security policies. At its most basic, a firewall is essentially the barrier that sits between a private internal network and the public Internet.
Exploit
An exploit is a piece of code, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability in an application to cause unintended or unanticipated behavior to occur on computer software, hardware, or something electronic.
IP Address
IP or Internet Protocol address is a numerical label assigned to each device connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: host or network interface identification and location addressing.
Types of IP:
Private IP
Public IP
Virtual Private Network (VPN)
A virtual private network, or VPN, is an encrypted connection over the Internet from a device to a network. The encrypted connection helps ensure that sensitive data is safely transmitted. It prevents unauthorized people from eavesdropping on the traffic and allows the user to conduct work remotely. VPN technology is widely used in corporate environments.


